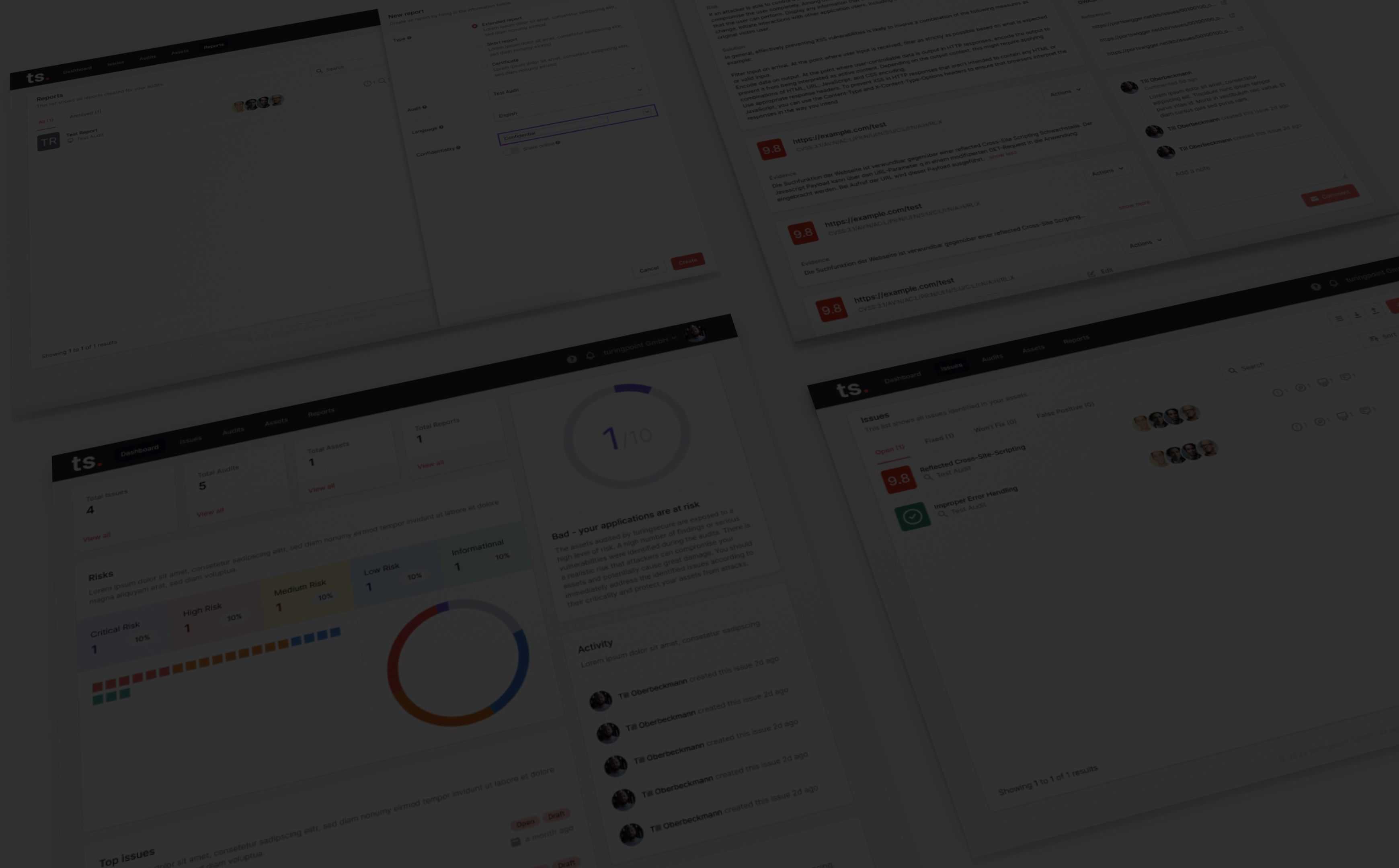
Deliverable Consistency
Effective methodologies, combined with rigorous in-app review and a well-stocked issue library of reusable, high-quality standards, streamline the pentest process and ensure consistent quality. The ability to import CSV data into the system further enhances efficiency, making it easier to manage external sources of vulnerbilitiies.




Consistent high-quality
Deliver Consistent Pentest Results with Us
Instead of relying on shared folders, access pre-loaded testing checklists and security methodologies like (OWASP, OSSTMM, BSI, PCIDSS, SANS SWAT, HIPAA, NIST und PTES) directly within your project. In addition, from physical pentests to smart contract audits and phishing simulations – our platform allows you to create customized templates for Standardize your approach and streamline your workflow.
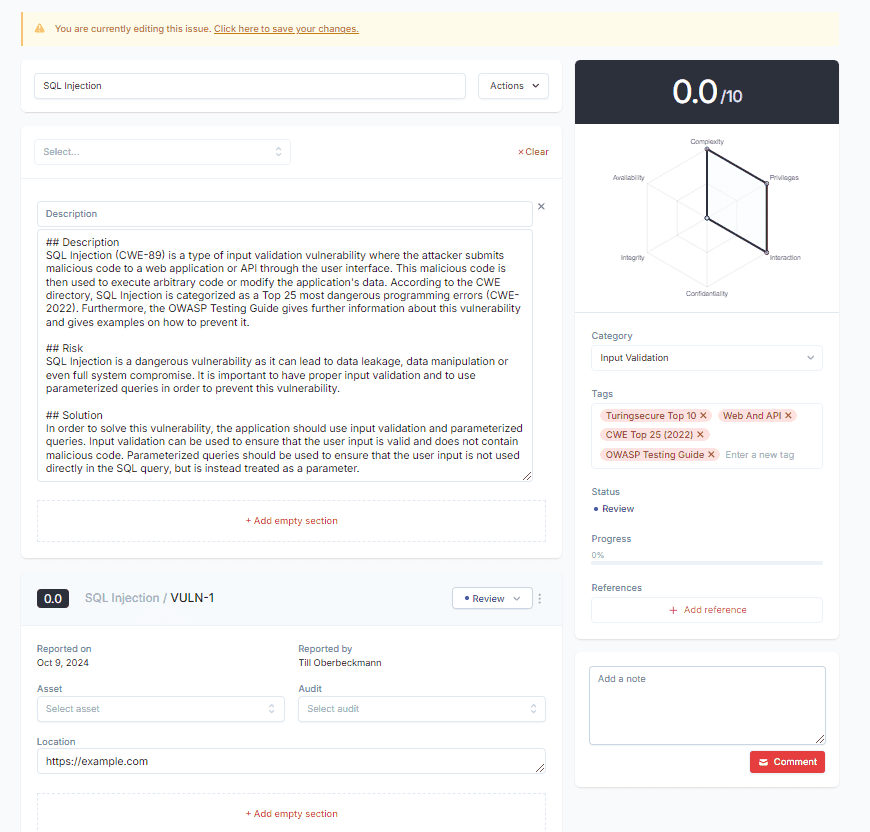
Ensure High Quality
Highly Automated Deliverable Consistency Accros Your Needs!
Create a template for issues for each type of assessment you perform.
Unified Data Schema
Our platform offers a unified data schema for vulnerabilities, enabling effortless export and import across different tools and systems. This standardized approach streamlines your vulnerability management processes and enhances interoperability.
Integrity in third-party software
turingsecure integrates with your existing management tools to provide you with real-time updates and actionable insights. Stay on top of the latest security threats and vulnerabilities so you can proactively respond and protect your organization.
Use External Sources to Identify Vulnerabilities
Streamline your workflow with automated integration of security scanners. Process findings from popular tools like Burp, Nessus and Greenbone seamlessly.
Curious? Convinced? Interested?
Arrange a no-obligation consultation with one of our product experts today.
