Vulnerability Disclosure Bug Bounty Program
Bug bounties motivate hackers to find vulnerabilities in software. Fair treatment and appropriate remuneration encourage them to report the gaps to the company.





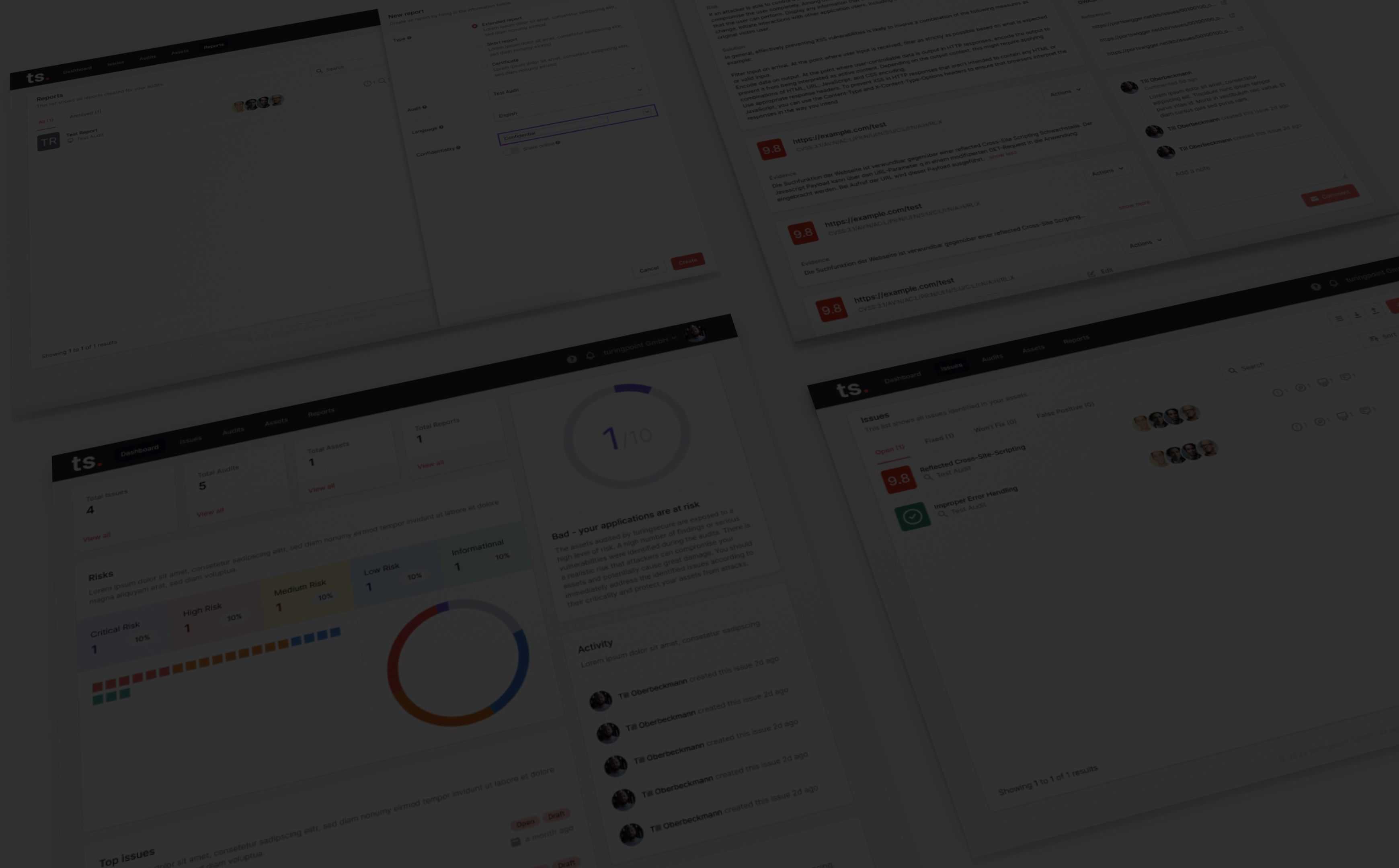
Vulnerability and Incident Reporting Process
Vulnerability Disclosure
It is essential that software or hardware vendors can quickly fix vulnerabilities before malicious actors can find and exploit them. Our Vulnerability Disclosure describe the process for security researchers to securely report vulnerabilities. The identified vulnerabilities are then directly reviewed for accuracy and communicated to the appropriate stakeholders in the organization.

Tenders for Bonuses
Bug Bounty Program
Collective vulnerability identification is essential, so bug bounties that reward researchers for finding vulnerabilities.
Often, bug bounty programs are implemented along with internal code audits and penetration testing as part of an organization's vulnerability management.

Take part in Our Program!
Reward for Vulnerability Disclosures
The Advantages of a Modern Bug Bounty Program
Why should your company participate in a Bug Bounty? In short: You get scalable and profound knowledge from an agile process that is designed to be transparent and, above all, effective.
Scalable Cyber Security
Provide all the information about your IT systems so that you can draw on the in-depth knowledge of all security researchers.
Transparent & Effective
Show your customers your commitment to security. Build trust through your public bug bounty programs.
Infrastructures
The pentest for critical IT infrastructures (KRITIS) tests the security of e.g. server systems, VPN systems, WLAN networks and firewalls. As a basis for secure applications, the system as well as the network infrastructure must not be neglected.
