Penetration Testing Protects Your Company from Hackers!
Highly qualified pentester with modern solution approach!
Above average quality with over 150 penetration tests per year.
Clear vulnerability management with remediation steps.





WHY PENETRATION TESTING?
Penetration Testing as an Effective Security Solution
Our experienced IT security consultants uncover vulnerabilities in web applications, mobile apps and IT systems before a real hacker can exploit them. Reduce remediation costs, network downtime and preserve your company's image with the customer loyalty that comes with it.
Your benefits with us:
- Experience with current cloud technologies and the specific security requirements of the industry.
- Execution according to recognized Standards (e.g. OWASP) and testing methodologies such as WhiteBox, GreyBox or BlackBox.
- High level of professionalism - Accredited to ISO 27001 and the OSCP certificate.
- Optimized reports with clear recommendations for action and further services in the field of cyber security.
- Interactive implementation possible in close coordination on the platform.
- One-time free review and certification of cyber security.

THE PROCESS OF IMPLEMENTATION
Procedure of a Penetration Test with You
In a penetration test, we put your software and hardware through their through its paces. Our security engineers use a range of different methods to find and test vulnerabilities. The final step is the report which lists the vulnerabilities found and specifies the risks for your company. for your company. The report is your guide to more security for your systems.
Planning: Set the Framework
In the kick-off meeting, we jointly define the framework conditions for the pentest.
What is to be tested?
Who are the contact persons?
Which access paths will be used?
Subsequently, our security engineers start collecting information. In doing so, we rely on a broad portfolio of direct and indirect methods to identify as many attack vectors as possible.
Implementation: Testing for Vulnerabilities
After gathering information, the actual penetration testing begins: Our security engineers try to exploit the identified vulnerabilities. They either use publicly available exploits or use their own developments, to gain access to the target system.
We follow the practical guide for pentests from the BSI and the provisions of the DSGVO. the DSGVO. Upon request, we align our tests with other standards: OSSTMM, PTES and OWASP.
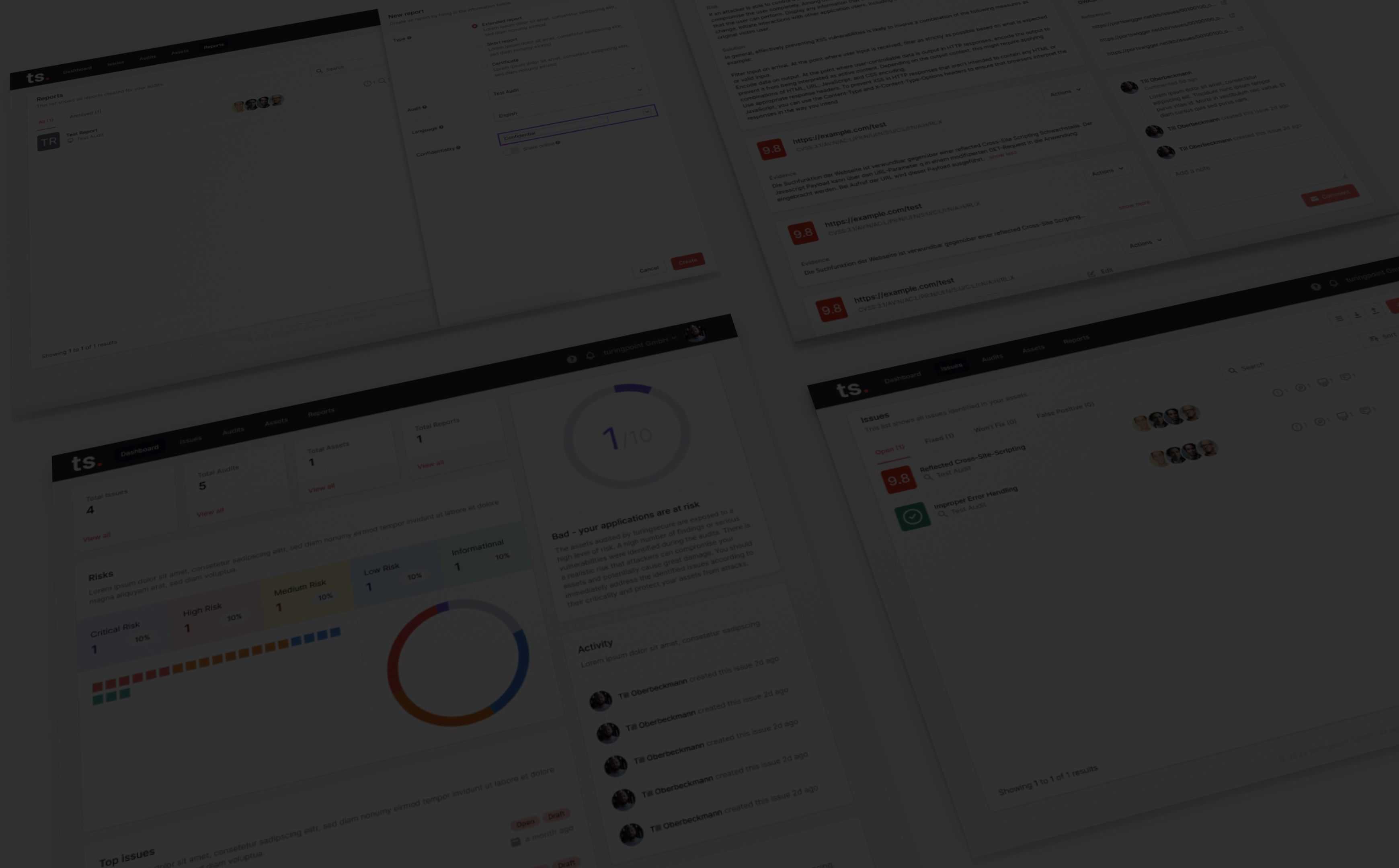
Conclusion: Interactive Report and Dashboard with follow-up Services.
All verified vulnerabilities are described in detail in the report and are listed according to their Criticality according to CVSS 3.0 and presented in a graphically understandable way.
In the business risk analysis we evaluate the verified vulnerabilities in terms of the potential damage to your company. The management summary describes in short, simple words the core of the report, so that all decision makers can be easily informed about the results.
PENETRATION TESTS ON TURINGSECURE
Scope of the Penetration Test with the Individual Phases
In penetration testing, we put your software and hardware through its paces. Our security engineers use a range of different phases to find, test and document vulnerabilities. The final step is the report, which lists the vulnerabilities found and specifies the risks to your company. The report is your guide to more security for your systems.

PENETRATION TESTING FOR ALL DIGITAL SYSTEMS
IT Security in All Areas
We provide a range of penetration tests covering all digital systems.
Web Penetration Test
Web applications often reach deep into a system. As a result, there are more attack vectors that are directly tied to the IT infrastructure.
Mobile Penetration Test
We subject your mobile app to various tests, check the security of the configuration and communication with the server.
IT-Infrastruktur Penetration Test
The IT infrastructure is the basis for secure applications and sustainable business success
Cloud Cyber Security
Due to the increasing complexity of cloud infrastructures, many services are misconfigured. We help you identify and eliminate misconfigurations and their impact on cloud security.
Static Code Analysis
Static code analysis, also known as source code analysis, is typically performed as part of a code review and takes place during the implementation phase of a Security Development Lifecycle (SDL).
Smart Contract Audit
Smart contracts are programs that are executed in a decentralized manner by each participant in the network. Therefore, smart contracts require more careful audits because they are economically rewarding targets for hackers.
Play it Safe
Our experienced IT security consultants uncover vulnerabilities in web applications, mobile apps and IT systems before a real hacker can exploit them. Reduce remediation costs, network downtime and preserve your company's image with the customer loyalty that comes with it.
PENETRATION TESTS FROM TURINGSECURE.
Have Penetration Tests Performed on the Platform!
Arrange a free consultation with our security experts now
- Proven processes and trained experts
- Benefit from many years of experience! Penetration tests are planned, performed and evaluated by our specially trained security engineers according to recognized standards. In this way, we master the order-specific requirements every time and flexibly master new challenges.
- Reports that really help
- The final report is the tool for your company to plan efficient security measures and close security gaps. It provides a guide for investments in IT security and is thus the basis for sustainable security.
- Intensive consideration of complex business logic as well as extensive authorization structures
- The high testing intensity of our scanner software is a great benefit to the security budget and is consistent with the attack vectors from the OWASP Testing Guide. Our scanners very reliably find client-side vulnerabilities in single-page applications based on all technologies
- Certification for your company
- Our pentest creates a double added value. Besides more security for your system, we have developed an effective certification system. The certificate can be integrated directly into your website and sends a clear message to your customers: "You are safe with us!"
Curious? Convinced? Interested?
Arrange a no-obligation consultation with one of our product experts today.









