End-to-end Encryption in the Browser
Modern software-as-a-service solutions use modern cloud technologies and cannot be installed as on-premises software. Due to regulations and compliance requirements, many companies are not allowed to use these software solutions, even though they generate great added value for process efficiency and quality.

Table of Content
In order to offer our customers and partners the best possible product despite these regulations, we have developed a framework that encrypts and decrypts data in the browser. Thus, the data can only be viewed by authorized users. The platform can thus be used without the developers or the operator, in this case us, being able to see the data!
The Technical Structure of Our Solution
The following program flow charts show the technical structure for the validation of our system. The activities highlighted in yellow represent an interaction with AWS Cognito and the Dynamo DB. The other activity is executed locally in the browser.
PAP:
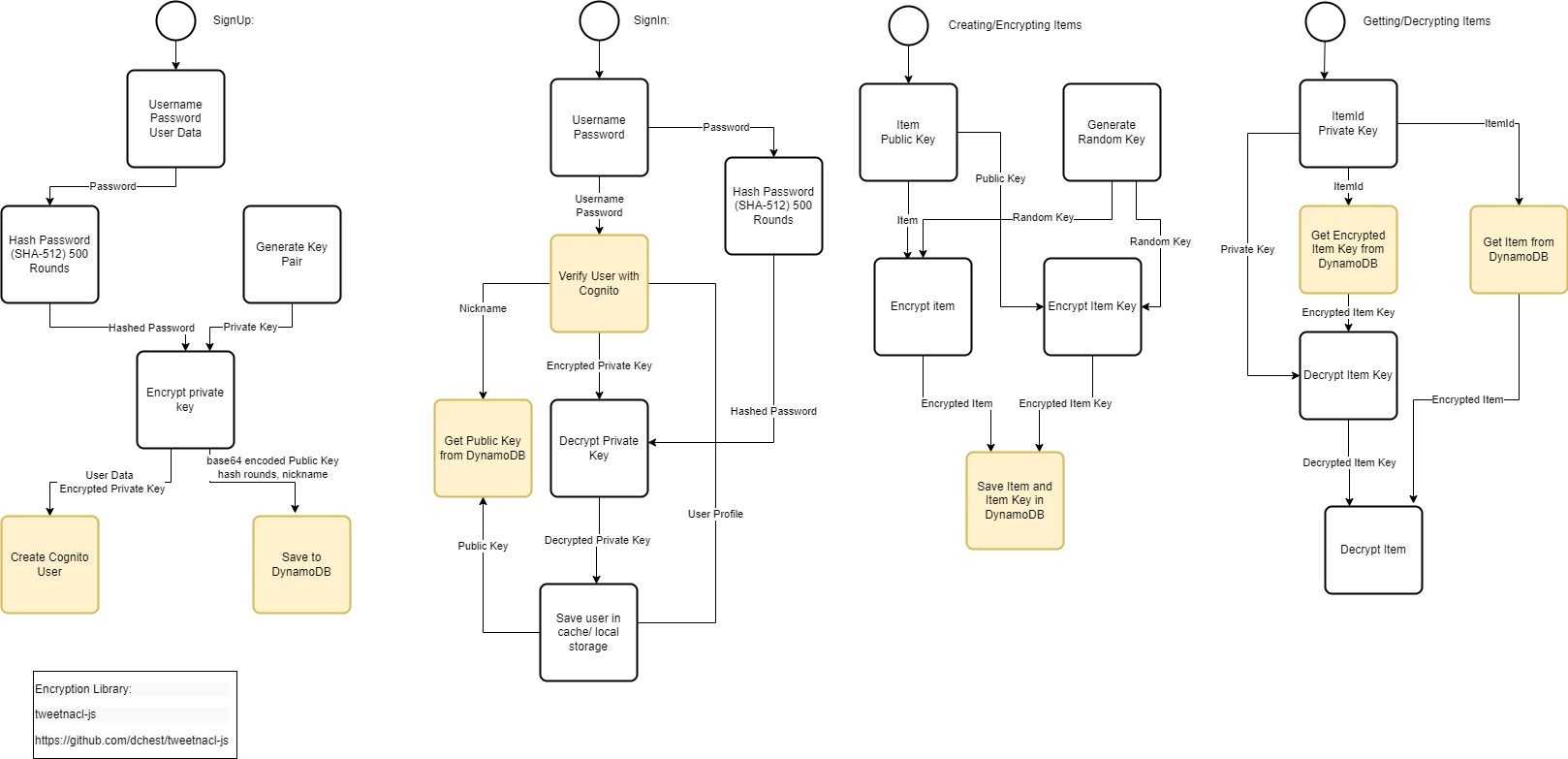
Create account
First, the user selects their username and password to the specific user data. After the password is hashed, it is encrypted along with the user's randomly generated key pair. The hashed password and the encrypted key pair are then stored in AWS Cognito along with the user data. The public key pair is stored unencrypted in the Dynamo DB.
Login
To log in to the platform, the user must be authorized by AWS Cognito. The encrypted Key Pair to decrypt data is decrypted with the password. After that, the data can be decrypted and read by the platform. The public key pair can be retrieved by username via Dynamo DB.
Encryption
A data set is encrypted with a randomly generated key. This key is then encrypted with the public key of the target users. Together with the encrypted data, this randomly generated key is stored encrypted in the Dynamo DB.
Decryption
To decrypt a record, the user needs their private key and ItemId. First the encrypted randomly generated key is decrypted with his private key, then the data set is decrypted with this key.
Cryptography Used
AWS Cognito
AWS Cognito uses the secure remote password (SRP) protocol as an extended Password Authenticated Key Exchange Protocol (PAKE) specifically designed to circumvent existing patents.
An important property is that an intermediary cannot obtain enough information to guess a password by brute force without further interaction with the parties in each (few) attempts. This means that high security can be achieved even with weak passwords.
Library Used
The cryptography used comes from the ttweetnacl modern JavaScript library (https://tweetnacl.js.org/#/). This has already been audited by finding no security problems and is actively maintained. (https://cure53.de/tweetnacl.pdf)
Curve25519
Curve25519 is an elliptic curve used for our asymmetric cryptosystem. It is particularly fast and standardized by the IETF as RFC 7748.
The curve is used by ProtonMail, Signal app, Threema, WhatsApp, Element, the Tor and I2P networks. The curve can be found in all popular libraries and can be used freely.
Salsa20
Salsa20 is a stream cipher developed by Daniel J. Bernstein in 2005 and is free of patents. Salsa20 usually provides better performance than the more common AES algorithm ( Advanced Encryption Standard ) on systems where the CPU lacks AES acceleration
Poly1305
Poly1305 is a cryptographic message authentication code (MAC) developed by Daniel J. Bernstein. It can be used to verify the data integrity and authenticity of a message. A variant of Bernstein's Poly1305 that does not require AES was standardized by the Internet Engineering Task Force in RFC 8439.
SHA-512
SHA-512 is a cryptological hash function known by the generic term SHA-2. As a hash function, it is used to provide digital files (e.g.: messages) with a hash value (digital signature). The number 512 stands for the length of the hash value in bit. The function is available in all common libraries and can be used patent-free.
Curious? Convinced? Interested?
Arrange a no-obligation consultation with one of our product experts today.
