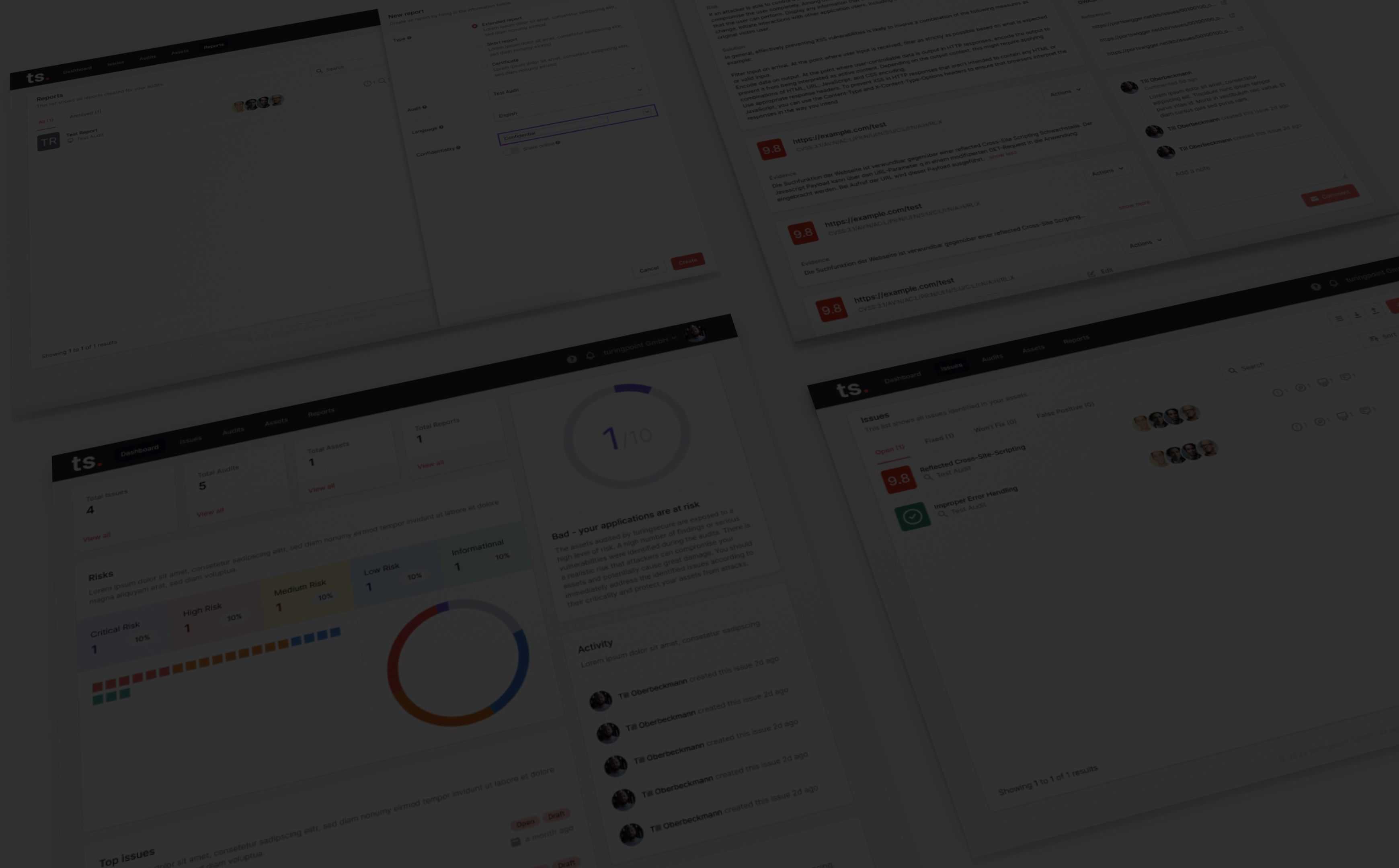
Attack Surface Management: Classify Attack Surfaces
Classify attack surfaces and gather attacker intelligence to implement proactive hardening measures.
Identify, Manage, Learn & Recover
Proactive Information Gathering with Early Warning System
Dynamic inventory of external IT assets and their vulnerabilities in a management board. Monitoring the attack surface is essential for risk management information gathering. Further target-oriented services can be built on this basis.

Attack Surface Management
Catalog & Monitor Dynamtic Surfaces
The flip side of pervasive digital transformation and increased use of remote workplaces due to the pandemic is that malicious actors are given more opportunities to attack. Security boundaries are no longer clear, and the range of potentially compromised enterprise resources is dynamically increasing.
Vulnerability Management for Transparency
Use our workflows to identify your IT assets. These include not only classic systems but also configurations, cloud systems and applications. Relationships between vulnerabilities and assets as well as their risks can be mapped.
Proactively Identify and Mitigate Changes
Detect changes to your IT infrastructure! Mitigate or harden the attack surface based on the vectors. Many insights can be gained through our threat intelligence.
Support Function for Risk Management and Cyber Security.
We help you derive new strategies from the findings and understand the outcome. Our platform provides CVSS classification and vulnerability combination for better understanding of the risk.
Navigate Efficiently Through Complex Infrastructures and Configurations
Cyber Security Plattform
Scalable Protection for Your IT Systems
Arrange a free consultation with our security experts now!
- Proven Processes and Trained Experts
- Benefit from many years of experience! Penetration tests are planned, conducted and evaluated by our specially trained security engineers according to recognized standards. In this way, we master the order-specific requirements every time and flexibly master new challenges.
- Reports that Really Help
- The final report is the tool for your company to plan efficient security measures and close security gaps. It provides a guideline for investments in IT security and is thus the basis for sustainable security.
- Protect Architecture Permanently
- There is no such thing as absolute security, because software is constantly evolving. With regular checks, we lay the foundation for lasting security of your architecture.
- Certification for Your Company
- Our pentest creates a double added value. Besides more security for your system, we have developed an effective certificate. The certificate can be embedded directly into your website and sends a clear message to your customers: "You are safe with us!"




