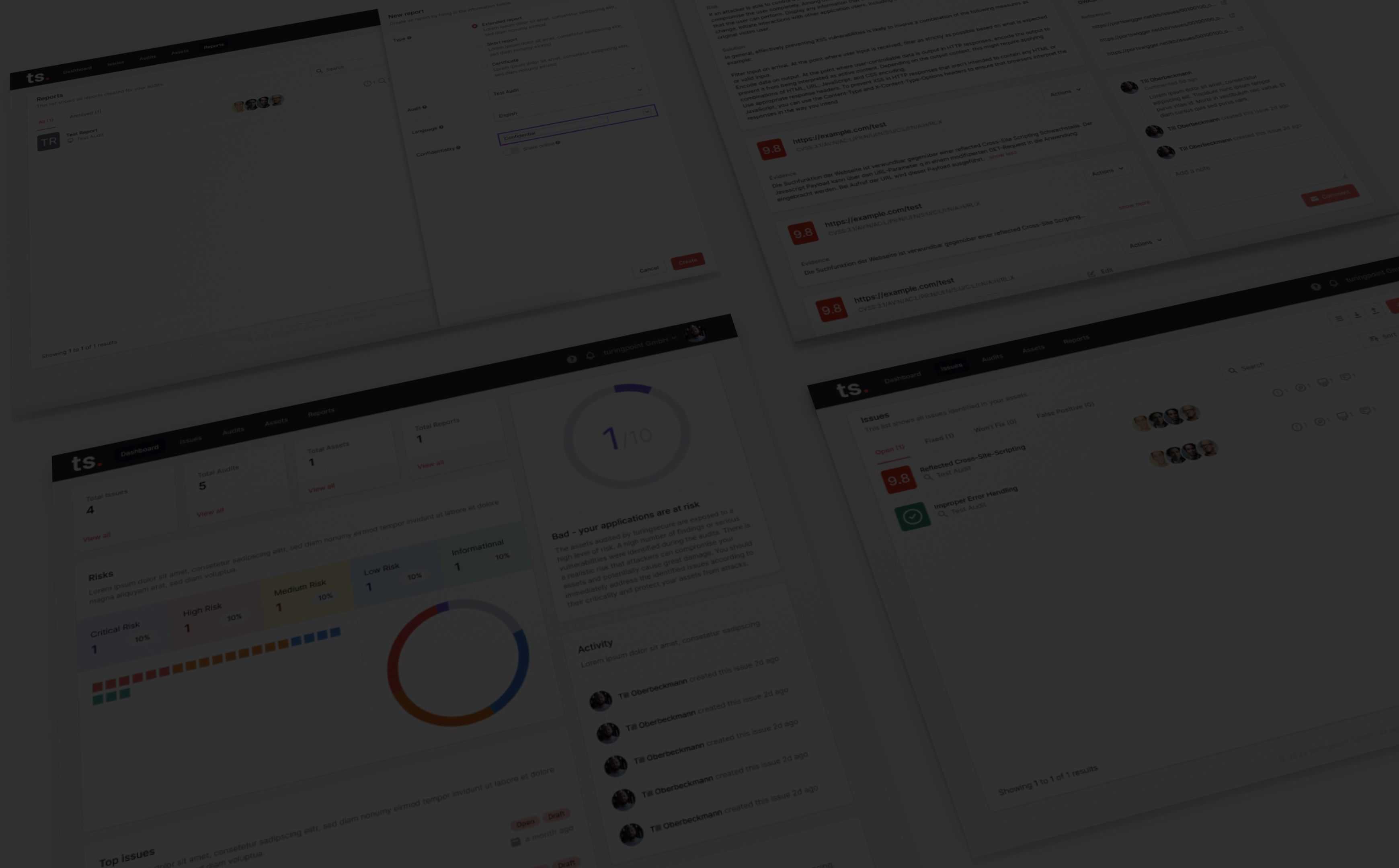
Security Visibility for Auditors, Compliance & Externals
To ensure cyber security visibility, it is important to invite third parties to audit the organization's security infrastructure. This will allow for transparency and help to identify any potential vulnerabilities. It is also important to ensure that there is no unnecessary communication with the auditors. This will help to keep the process efficient and focused.
Show Good Risk Management
Cyber Security Visibility with turingsecure
To ensure cyber security visibility, it is important to invite third parties to audit the organization's security infrastructure. This will allow for transparency and help to identify any potential vulnerabilities. It is also important to ensure that there is no unnecessary communication with the auditors. This will help to keep the process efficient and focused.
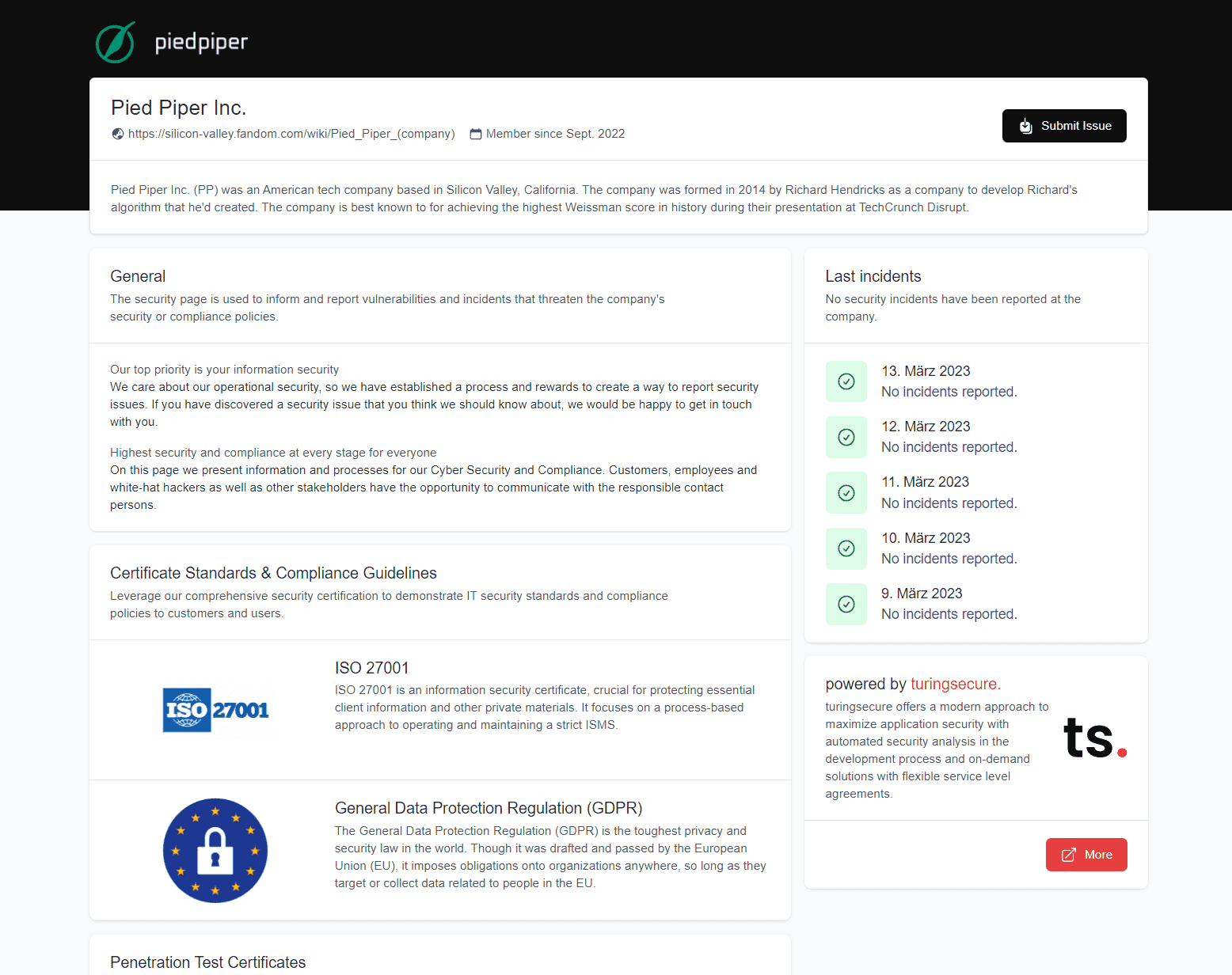
Guidelines, Transparency and Compliances
Compliance Confidence
To ensure that the security measures are understandable for everyone, it is important to create understandable dashboards. This will help to provide a clear overview of the security measures and any potential risks. Additionally, it is important to show your security guidelines and compliances to the auditors. This will ensure that they are aware of the measures taken and can provide an accurate assessment of the security infrastructure.
Overall, inviting third parties to audit the organization's security infrastructure is an important step in ensuring that the organization is secure. By having understandable dashboards and providing security guidelines and compliances to the auditors, the organization can ensure that the security measures are understood and any potential risks can be identified.
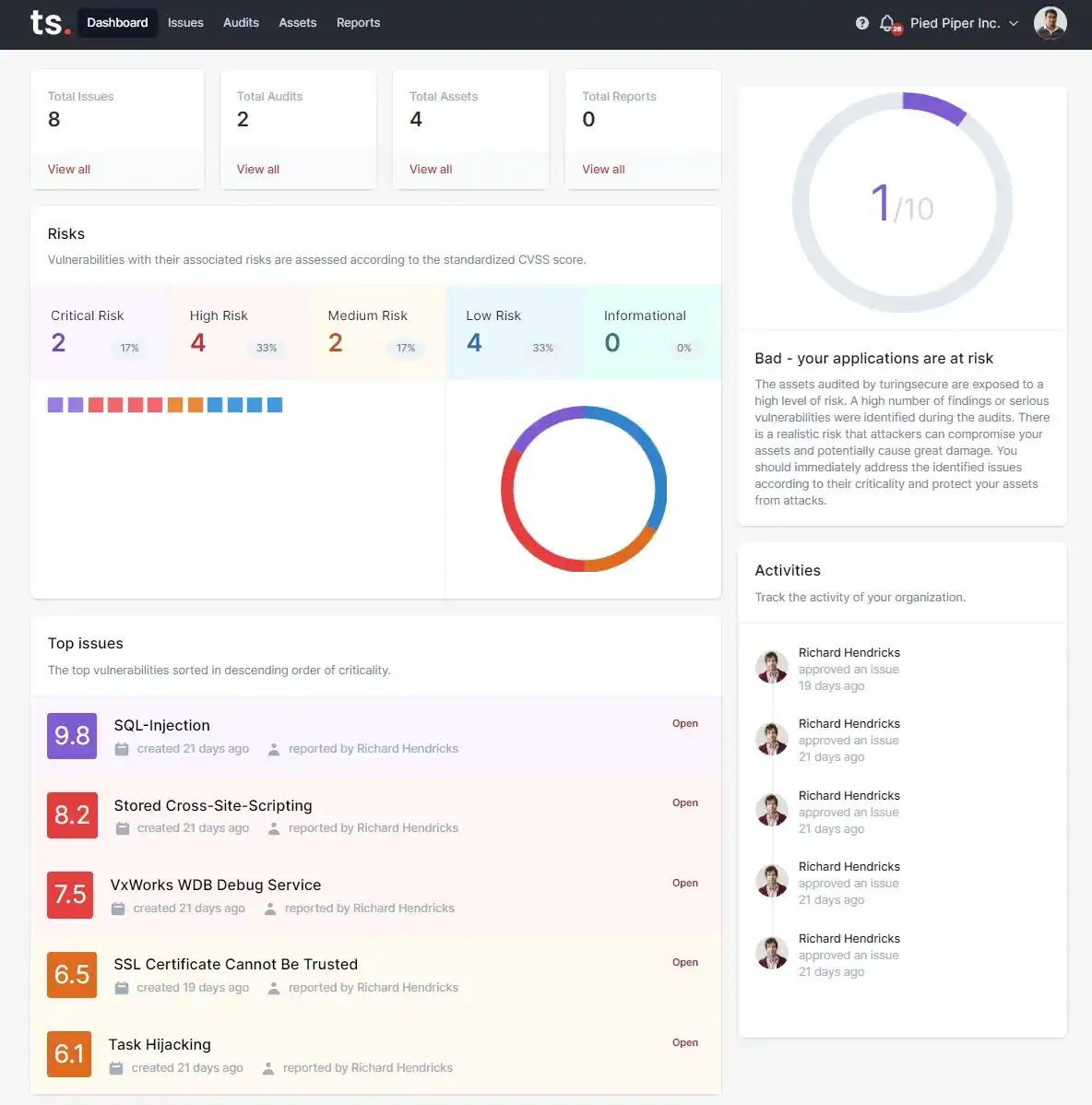
Present Your Effective Measures for Cyber Security and Compliance
Security pages are providing a comprehensive overview of the measures taken to ensure cyber security and compliance.
APPLICATION SECURITY AUTOMATED
Managed Automation Services with High Efficiency
We provide a set of automated security analytics that we manage and that can be augmented by manual activities, such as penetration testing.
Cyber Security Page Builder & Certificates
Integration of IT security through event- or time-based security checks in the lifecycle of the application. We guarantee a constantly high level of security through a modern DevSecOps solution.
Security Incident Response
View incidents in an IT context, accelerate investigations, and respond to threats with our expertise.
Penetration Testing
Our experienced IT security consultants uncover vulnerabilities in web applications, mobile apps and IT systems before a real hacker can exploit them.
Curious? Convinced? Interested?
Arrange a no-obligation consultation with one of our product experts today.



